Cloud And FinTech: Security Gaps Emerge
~7 min read

The adoption and use of cloud services is gaining traction among financial institutions as they gain confidence in cloud service providers’ capabilities in securely handling core infrastructure. However, emerging gaps in security between cloud service providers (CSPs) and financial service providers (FSPs) illustrate a difficulty in managing the network infrastructure when shared between multiple parties. The whos, whats, and hows of cloud security seem to get lost in implementation, leaving financial institutions vulnerable to cyber-attacks.
The Role of Cloud Services in FinTech
Cloud services are steadily becoming more integral to fintech ecosystems. A Foundry survey found that 34% of companies were using a mostly cloud-based infrastructure for their business, an increase from 29% just 2 years before in 2020. Traditional banks that relied on legacy systems have also been increasingly moving their functions to the cloud. Their investments in cloud services are on the increase, growing 3.5 times faster than the total IT spending among banks.
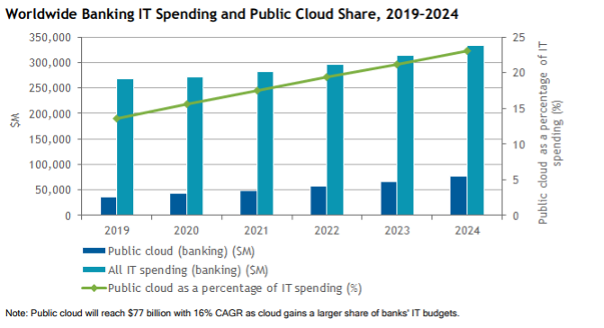
Source: IDC
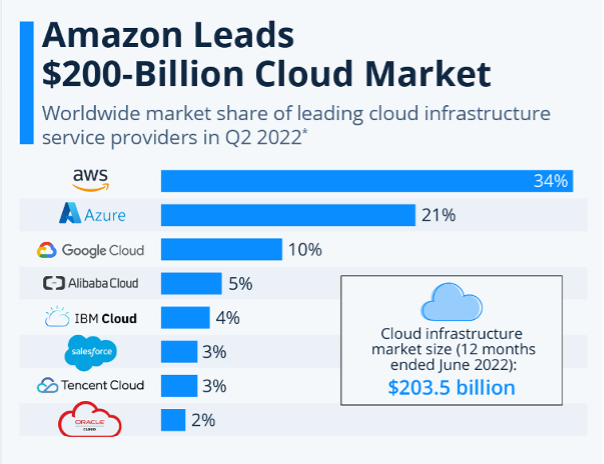
While there are multiple CSPs, the industry is dominated by only four industry players namely AWS, Microsoft Azure, Google Cloud and Alibaba Cloud. Two of these players, AWS and Microsoft Azure, hold more than half of the global market share, while Alibaba holds 25.5% marketshare in the Asia Pacific, making it an industry leader in the region. This domination by a handful of Big Techs has enabled greater standardization of protocols but also concentrated security risks among fewer baskets.
Fintechs and financial institutions that use the cloud can leverage data to provide personalized services to their clients and grow in tandem with the market while requiring less infrastructural investments on the road to upscaling, among other benefits of using the cloud. However, they also face the reality of shared responsibility between them and the cloud service providers (CSPs). The shared responsibility model that cloud users and providers use outlines the responsibilities of each party in securing data and the underlying infrastructure. Yet its implementation is tricky.
Shared Responsibility And Subsequent Confusion
The distribution of responsibilities between CSPs and their clients leaves exploitable gaps in security. Amazon offer a general view of responsibilities in which the CSP is responsible for the security ‘of’ the cloud while the client is responsible for security ‘in’ the cloud. The specific responsibilities vary depending on the CSP in question and the client's preferred service model. Cloud Security Alliance summarizes the typical responsibilities. Where a client uses the Infrastructure-as-a-Service (IaaS) model, they would be responsible for the data, its use, proprietary applications, Identity and Access Management (IAM) and firewall configurations. The CSP would then be responsible for the infrastructure, including the networking, hardware, software and facilities.

Source: CIS
While the CSP will outline the responsibilities of each party to their client, execution depends greatly on the understanding and capabilities of the client. This is where complications arise, with clients lacking understanding of such protocols, which leads to poor execution of their responsibilities. Further complications arise when a client uses multiple service providers, but this is actually quite common; Foundry found that only 16% of companies rely on a single CSP. Using multiple service providers with different shared responsibility expectations increases the chances of letting key responsibilities slip through the cracks in execution. The constant improvements and additions of functional services by CSPs further require an ever-present eye on the infrastructure by clients to ensure no change affects their security.
Numerous documented data breaches are cases in which the responsibilities on the side of the client aren’t always met, nor are they handled in the right manner. The Capital One hack, which led to a data breach that affected 100 million customers, was caused by a misconfigured firewall that opened up access to sensitive data to third parties. Capital One was one of the early adopters of the public cloud services among FSPs. It partnered with AWS, citing AWS’ security as a key reason for its choice. AWS's security would enable Capital One to focus on other areas like data management. However, their trust in AWS may have caused the lax approach to security, leading to the misconfiguration that went unnoticed until it was too late. Capital One ended up paying $80 million in fines and $200 million in class action damages.
Knowledge assymetries between the CSPs and the clients are a likely cause of security concern. With technological advancements, clients may fail to invest adequately in oversight of the services they utilize from cloud providers, increasing their vulnerability. Misconfigured IaaS occurrences similar to Capital One’s are not uncommon. A survey from 2019 found that there were about 14 misconfigured IaaS instances running at any given time, totalling about 2,269 per month. Further instances of expired encryption certificates have been recorded, as was the case with Equifax. The gaps in knowledge require attention from enterprises, which means at a minimum investment in training and a security team that keeps the company’s systems up to date.
A Systemic Risk?
On the other side of the shared responsibility, the cloud service providers also pose a risk for the financial sector. The market concentration of CSPs naturally leads to profound risks of systemic disruption. The level of preparedness of FSPs in the event of significant failure on the CSP side remains unclear. And while CSPs have previously demonstrated an ability to quickly get back up in the case of outages affecting multiple companies, whether this demonstrated ability would be similar in a significant, network-wide outage remains to be seen.
Source: Statista
The possibility of systemic risk has brought about deliberations on how to ensure financial sector resilience in case system-wide disruptions occur. A gap in the regulatory environment is the first that needs to be considered, with FSPs typically exposed to much stricter regulations than the companies actually storing and managing their data. One suggestion gaining traction is for authorities to regulate CSPs as critical infrastructure, similar to telecommunications and power. US lawmakers have taken an extra step to request that CSPs be regulated as ‘systemically important financial market utilities,’ a move that would invite scrutiny by the US government and increase the risk management standards to be met by CSPs. The move is, however, complicated to achieve as CSPs, unlike other utilities categorized as systemically important in the financial market, are not primarily financial actors. The particulars of potential regulations raise further questions. CSPs are diverse in the services, infrastructure, and facilities they provide. Should some CSPs be deemed systemically important, or some of their functions left alone, or should the entire cloud industry be applied with the same kind of scrutiny?
FSPs are also advised to err on the side of caution by outsourcing to providers who specialize in the finance space and seek services from different vendors. But finding CSPs that specialize in the finance sector and can adeptly handle core banking operations for traditional banks is easier said than done. Rather, most CSPs cater to multiple industries while providing tailored solutions for financial sector players. For smaller banks and fintechs, options such as Jack Henry and Fiserv offer cloud-based platforms, but these companies still rely on the big tech providers; Fiserv’s CRM management tool, Enteract, relies on Microsoft Azure, for example.
Enteract forms part of a larger group of Microsoft partners that offer cloud-based solutions to FSPs. Services tailored to the financial sector are popping up across the board. IBM has an in-house tailored cloud for financial services, while Google also has a cloud for financial services. While such services may provide financial service providers with key infrastructure that they need and make it easy for businesses to comply with regulations, they further increase the concentration of services among a handful of CSPs.
The concentration of cloud services among the handful of large tech companies isn’t all bad, especially in comparison to previous traditional legacy systems. As Ken Birman, a professor with a long history of work in cyber reliability and security shares, it doesn’t necessarily create a technical risk.
“It’s not necessarily good if every bank uses its own mix of [privately built] software because there can be cyber threats that no one else would have been aware of, that the companies that do cyber assurance wouldn’t really have looked at that mix of software tools. So the big benefit of the cloud is that the reduction in the diversity of choices actually means that the degree of assurance for these mixtures is much more carefully scrutinized.”
Ken Birman, Professor of Computer Science, Cornell University
Pitfalls notwithstanding, the use of cloud services does remain more secure than in-house systems. A strong team of in-house experts and collaboration with third-party security experts can enable end-to-end monitoring on the use of cloud services by FSPs. Bridging the security gaps isn’t impossible — only tricky and delicate, and something that the Big Techs alone won’t completely assure.
However, the shared responsibility approach is likely to change soon, as regulators assess the division of liability between the providers and their clients and whether systemic overhaul is needed. Efforts to delineate the shared burden may see the shared responsibility model codified or changed to enhance consumer protection. Yet in the interim, it remains incumbent for FSPs to not simply rest on their laurels knowing a Big Tech is overseeing their cloud infrastructure — in a world run by giants, the little guy must look out for themselves all the same.
Image courtesy of Julian Schiemann
Click here to subscribe and receive a weekly Mondato Insight directly to your inbox.

Travel And Fintech: Where Challenge Meets Flush Opportunity
The Conundrum Of Chargeback Fraud